web1
题目源码链接
https://d4n-picture-database.oss-cn-beijing.aliyuncs.com/img/CISCN+2019+web1.zip
访问:http://172.28.76.89:8845/CISCN_2019_web1/
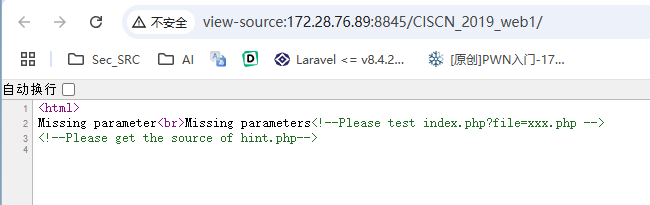
得到提示,利用伪协议获取hint.php和index.php内容
|
|
hint.php
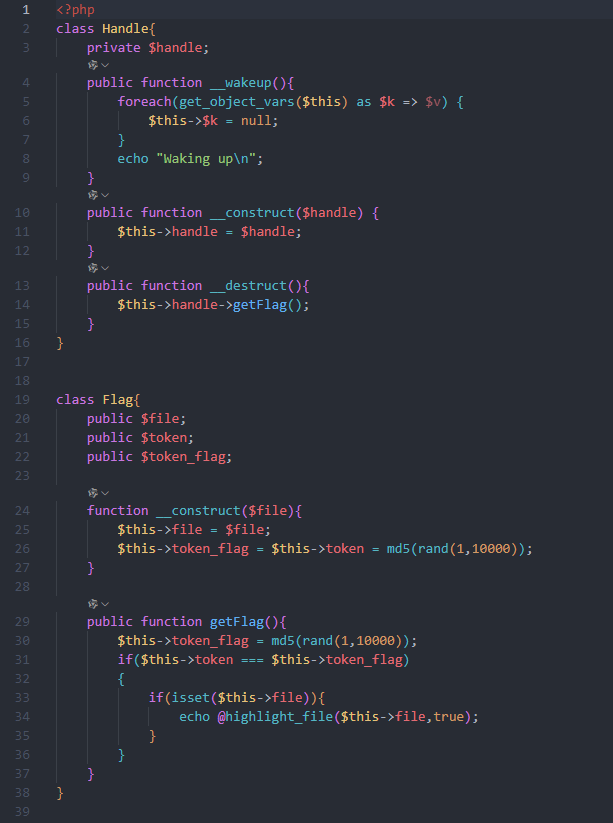
index.php
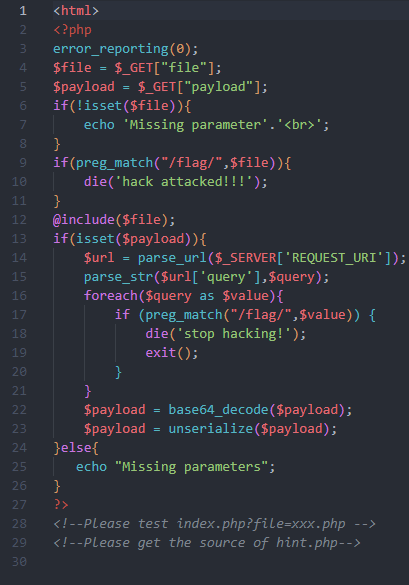
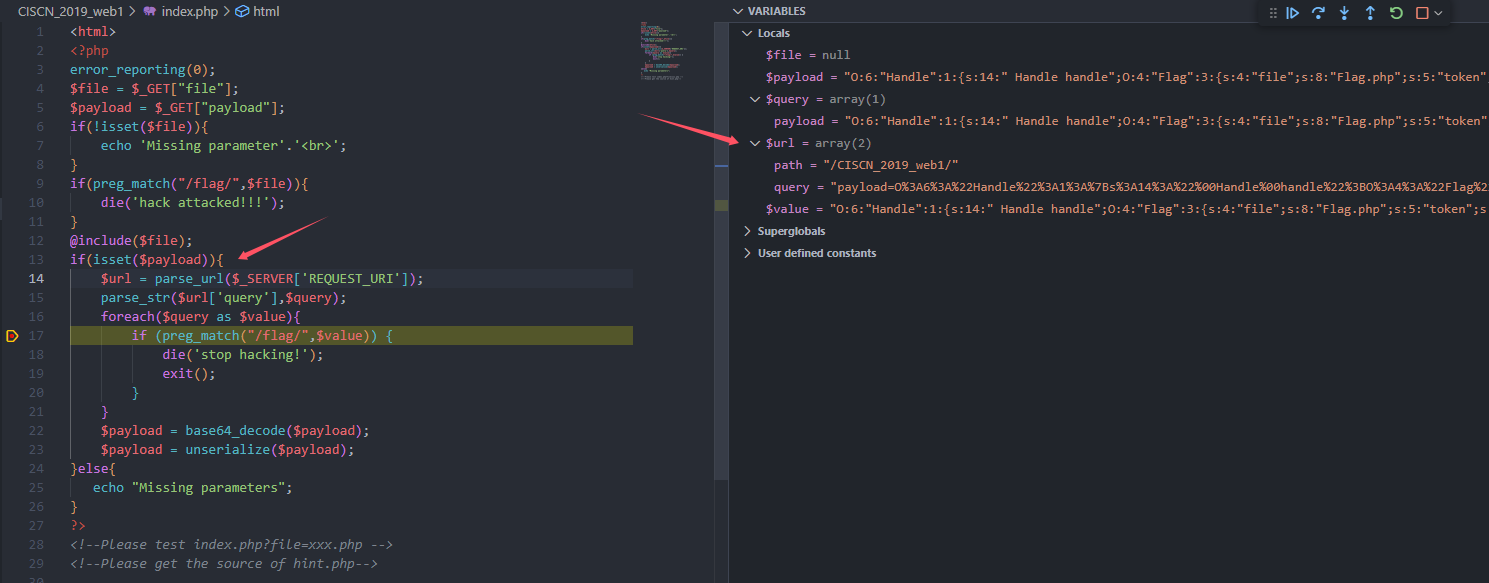
hint.php 包含两个类,index.php中包含unserialize(),固考虑反序列化利用
先根据目前的信息构造反序列化链
知识点
引用 Reference
在当前题目中,存在如下比较,关注行8和行13
|
|
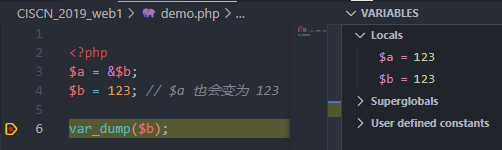
可以看到行8有一次链式赋值操作,但是在行13刷新了其中一个变量的值,那么此时,服务端想要两次随机出来的数一致几乎不可能,所以这里需要用到 引用 Reference
Demo
|
|
parse_url() 绕过
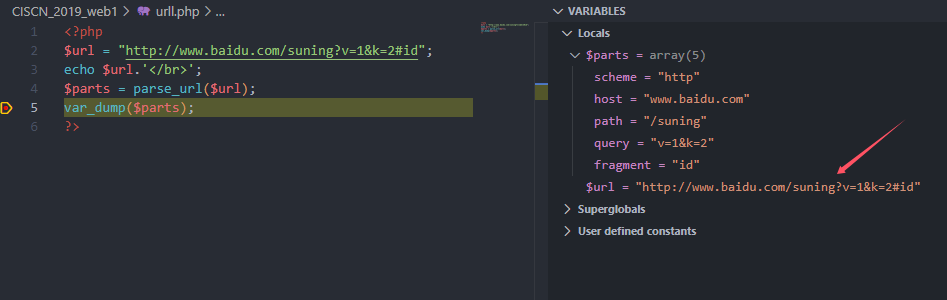
正常解析
input
|
|
解析为
但是输入为下时,可以进行绕过
input
|
|
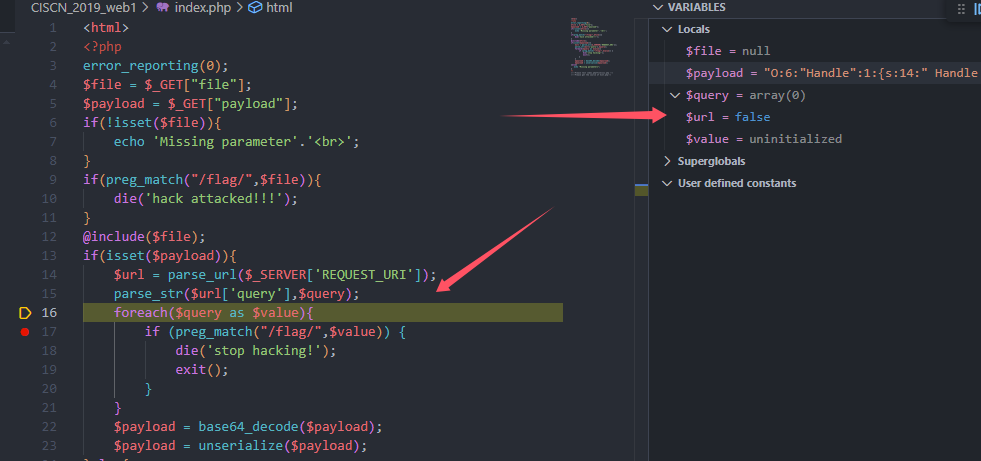
此时发现$query因为$url无法解析为false后,$query值也为空数组。
此时不会进入foreach,成功绕过
扩展
使其错误解析
Demo
|
|
正常解析
诱导解析 host
使用@
严格意义上来说不算错误,是人为输入诱导parse_url()输出错误的host
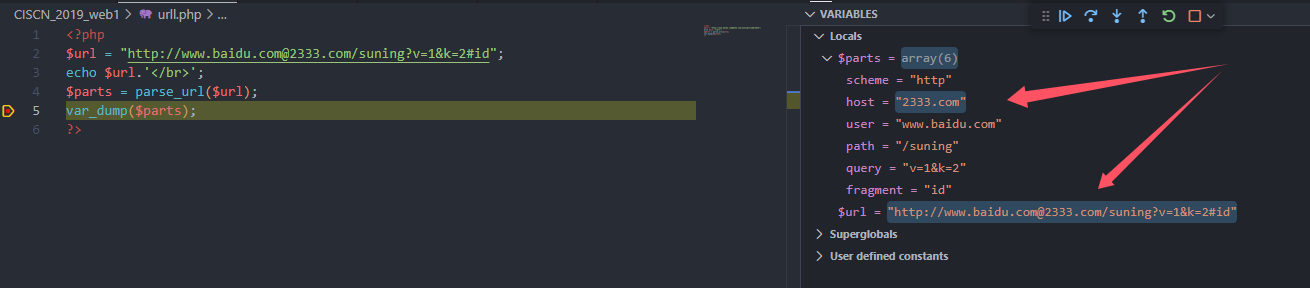
错误解析
正常情况
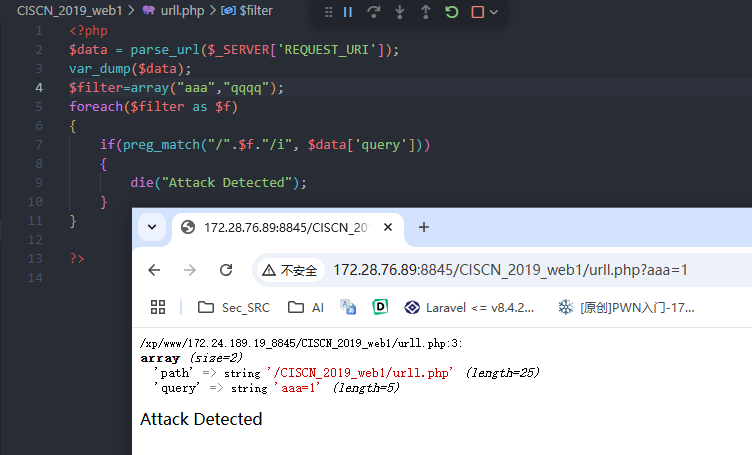
使用//,使其错误解析host
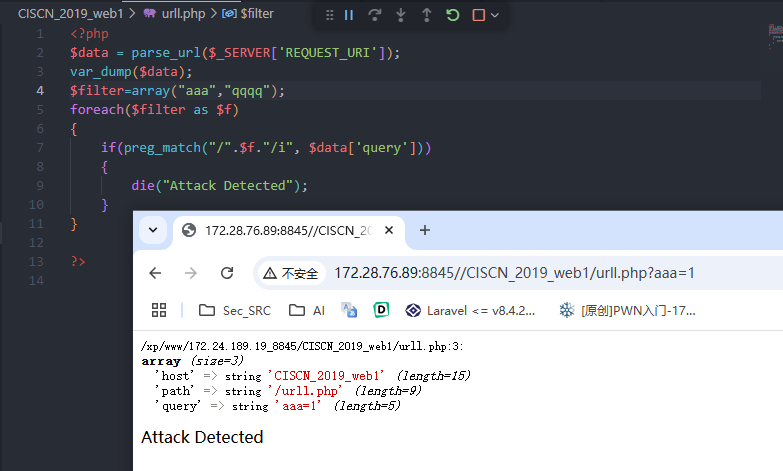
使其无法解析
Demo
|
|
正常解析
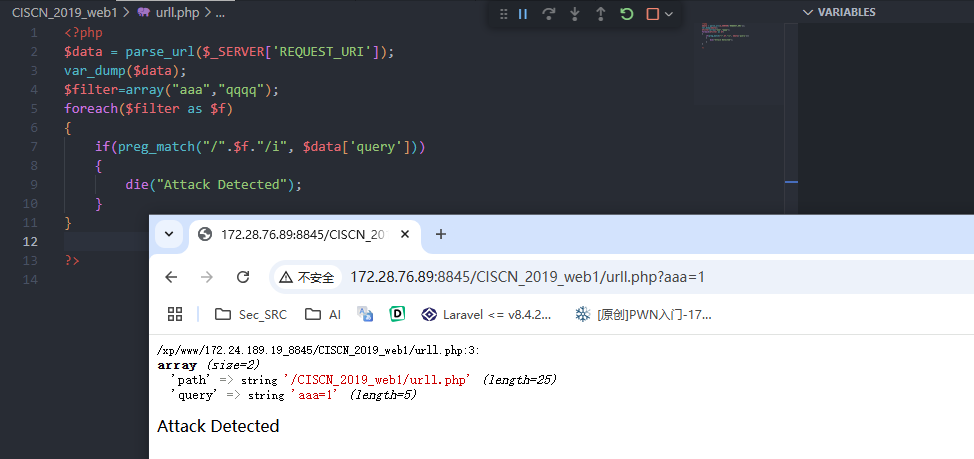
无法解析
使用 ///
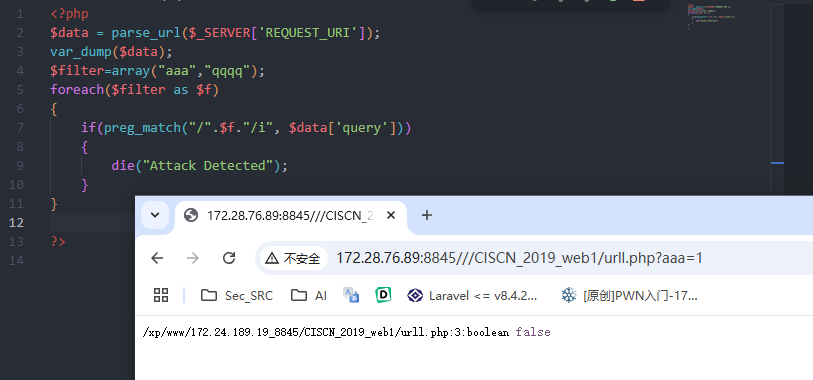
__wakeup() 绕过
CVE-2016-7124
使用CVE-2016-7124进行__wakeup()绕过
- PHP5 < 5.6.25
- PHP7 < 7.0.10
Demo
|
|
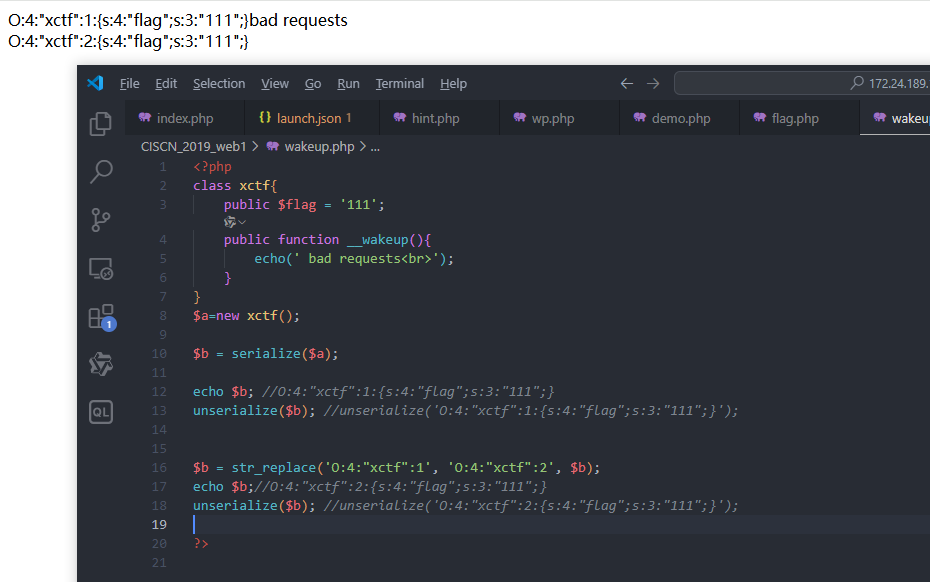
解题
php环境需满足这里
wp.php
|
|
input
|
|
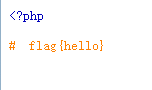
成功
web3
题目源码
|
|
知识点
进制转换绕过,构造_GET
base_convert(37907361743,10,36)(dechex(1598506324)) => hex2bin(5f474554) => _GET
$$特性
$$pi{0} => $_GET{0} => $_GET[0]
使用其他GET参数传递敏感值
$_GET[0]($_GET[1]) 配合 &0=system&1=ls%20-al 拿到执行函数与命令
解题
payload
|
|
